An Intro to Building Management Systems (BMS)
Before we dive into it, a Building Management System (BMS), a.k.a. “Smart Building Technology,” is an intelligent microprocessor-based controller network installed to monitor and control a building’s technical systems and services, (air conditioning, heating, video surveillance, elevators, etc.). These services are essential for managing industrial operations. BMS and centralized building management systems enhance the management of industrial infrastructures and a building’s mechanical and electrical equipment.
The BMS system also controls energy consumption, boiler controls, lighting controls, the fire alarm system, and the plumbing/water monitoring among other functions, with cost containment as the main focus.
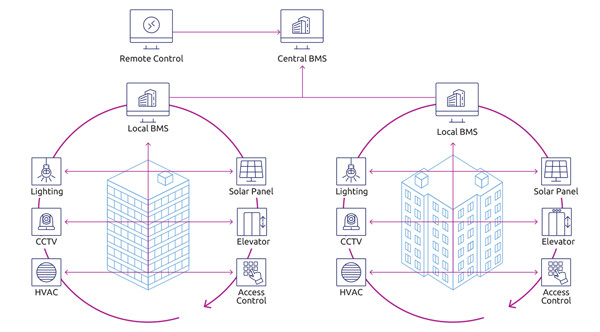
The different systems used in a smart building
The Rise of Smart Building Technology for BMS
According to ASIS International, the use of building management systems is growing at approximately 15% to 34% annually. By 2022, the building management system industry is expected to be worth around $104 billion.
Building management systems, are being implemented for an increasingly wide range of applications. While the initial BMS systems were for heating and cooling and primarily used to reduce costs, today a huge range of smart devices is being leveraged to increase worker productivity, reduce operational costs, and secure businesses. While the headlines only catch the high-profile new smart buildings, the truth is that new BMS technologies are making their way into just about every type of structure.
BMS systems are also used to monitor and secure hospitals, data centers, airports, and hotels.
Security Risks of Smart Building Technology
Although BMS systems were never designed to be connected to the internet, it’s unrealistic to think they would remain as closed systems. In fact, the increasing number of interconnected smart devices opens them up to so many access points that it’s impossible to keep them isolated. Therefore, alongside the tremendous operational benefits of smart building technology, all these new devices, and their interconnectivity introduce new cybersecurity risks.
With hundreds of thousands of devices in a building, the potential attack surfaces from unsecured devices are enormous, and the implications of the attacks can be more dramatic.
There have been a few high-profile cyberattacks on businesses via a building management system. One instance was the BMS cyberattack against Target. Cyber attackers gained access to Target’s point-of-sale (POS) system software to obtain the credit and debit card data associated with over 110 million accounts.
The hackers did not directly attack the POS system. Instead, they began by stealing login credentials used by Target’s heating, ventilation, and air conditioning vendor when they connected to the target web applications. It was through this attack vector that the hackers gained access to Target’s Active Directory and, ultimately, the Target POS system where they could collect credit card numbers and other sensitive data.
Other Examples of how BMS Systems can be Attacked:
- Ransomware attacks can take control of critical systems, such as in this case of a hotel in Austria, where hotel residents were locked out of bedrooms.
- Denial of service attacks can overload smart building systems and disrupt critical systems such as heating during cold winter days.
- Smart devices can be hacked to get access to the main IT systems of the entire company.
BMS systems are considered Operational Technology (OT), and they differ from standard IT systems primarily because of the variety of devices, protocols, and functionalities of the networks. BMS systems include embedded technologies that generate data, perform physical functions, and communicate using industry-specific OT protocols such as BACNet attacks and LonWork. Given the BMS-specific protocols and the variety and multitudes of devices involved, the challenges of smart building security need to be addressed directly with security solutions designed specifically for those challenges.
BMS: The Unique Challenges of Smart Building Technology
The main distinction between BMS networks and other OT networks like in factories, for example, is that smart buildings do not have a well-defined physical perimeter. Environments with BMS networks are characterized by a large number of visitors inside the physical perimeter. In an office building, hotel, apartment complex, or even a hospital – hundreds or even thousands of guests may visit daily.
The definition of the access permissions constantly changes, increasing the possibility of breaches. It becomes overwhelmingly difficult to identify anomalous behavior. OT systems are generally spread all across a facility with many networking and access points, allowing various interfaces with the BMS network.
Another difficulty is comparing BMS networks to Industrial Control Systems (ICS) and believing that smart building security can be controlled like ICS security. Quite the contrary, BMS networks are much more interconnected than ICS networks. Additionally, the Internet of Things (IoT) devices are an important component of smart buildings and are less likely to be found in ICS systems.
Increasing Control and Visibility in BMS Networks
To meet the security challenges of BMS networks, it is essential to have security systems that can discover every single device on a network, detect any rogue devices, and detect activities that can endanger the operational stability of these critical devices.
By monitoring OT network traffic and behavior and by analyzing proprietary BMS protocols such as LonWorks and BACNet, the idyllic solution quickly identifies and monitors every single device in any network and provides 100% monitoring of all traffic from all devices.
Security teams for BMS networks need to integrate a proven BMS security solution into each subsystem, such as access control and elevators or on each floor of a building. Once they’re connected to the BMS network, the platform provides the visibility and monitoring capabilities required to gain control over their large-scale complex environments.
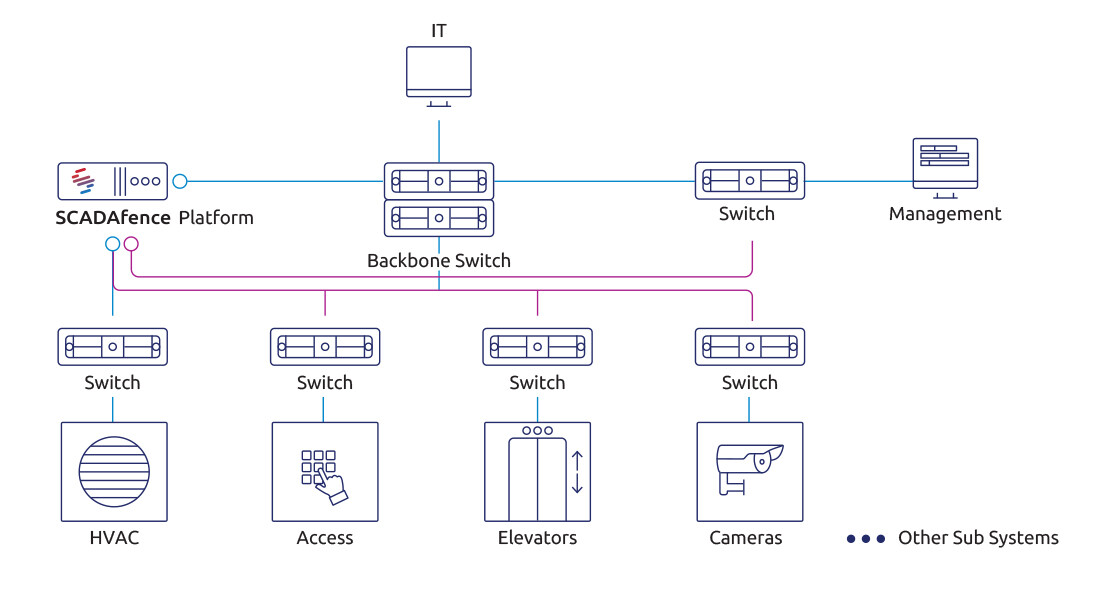 The network diagram for the BMS Security Solution
The network diagram for the BMS Security Solution
What Core Benefits Should a Perfect BMS Network Security Solution Include?
- The ability to offer discovery and inventory management of all the devices throughout the building or campus.
- A full, deep packet inspection support for proprietary BMS protocols such as LonWorks and BACNet.
- It should be a non-intrusive/agentless monitoring system with zero influence on the performance of the smart devices in the network.
- It should have an adaptive, dynamic baseline that will learn about normative behavior and automatically detect any anomalies or potentially malicious network behavior.
- It should be future proof, meaning that as BMS architecture develops, the ability to adapt immediately to new configurations and devices should be automated.
- It should secure critical systems such as HVAC, elevators, surveillance and access control.
- It should be easy to use and operate for both OT staff and IT staff.
- Finally, it should seamlessly integrate of BMS OT security into existing security controls.
SCADAfence will secure Japan’s 2020 Olympics with their BMS security solution and are currently working with multiple global real estate developers and smart cities to keep them secure.



