Co-written by Ofer Shaked and Maayan Fishelov
Background
Odveta is a ransomware that has been observed in multiple industrial networks. It doesn’t have an automated propagation mechanism, and it is usually used in targeted attacks by cybercriminals. A ransom note is created and placed on every folder including the desktop, with instructions on how to pay the ransom using Bitcoins.
Odveta is a variant of the King Ouroboros ransomware which is based on an open-source ransomware project called CryptoWire. Unlike the previous versions, Odveta uses RSA+AES256 encryption, rather than only the use of AES in previous versions. The old variants contained an encryption flaw that could be decrypted using a decryption tool. Unfortunately, Odveta uses RSA+AES256 encryption and up to today, there is no decryption tool, making the encryption irreversible.
Infection methods
Odveta is delivered via email attachments, torrent websites, and malicious ads. It is also delivered via the RDP exploit BlueKeep.
Technical Analysis
The OT ransomware first generates an ID that is unique per run. This ID identifies the victim and is sent with the encryption key to the C&C server.
This allows the attackers to decrypt a single file to show the victim that they are able to decrypt the files. The victim can send an email to the attackers with one of its encrypted files and get back the decrypted file from the attackers.
Processes Termination Service Stopping
Upon initial run, Odveta is stopping the following service using the “net stop” command
- SQLWriter
- SQL Browser
- MSSQLSERVER
- MSSQL$CONTOSO1
- MSDTC
- SQLSERVERAGENT
- MSSQLSERVER
- SQLSERVERAGENT
- MySQL
Process termination
- sqlserver.exe
- msftesql.exe
- sqlagent.exe
- sqlbrowser.exe
- sqlwriter.exe
- mysqld.exe
- mysqld-nt.exe
- mysqld-opt.exe
File Encryption
Odveta encrypts all files using RSA+AES256 encryption algorithms.
After encryption files are renamed with the following pattern
[filename].Email=[Email]ID=[infection_id].odveta
“filename” – original file name
“email” – attacker’s email, the way to communicate with the attacker
“Infection_id” – identifies the victim.
Ransom Note
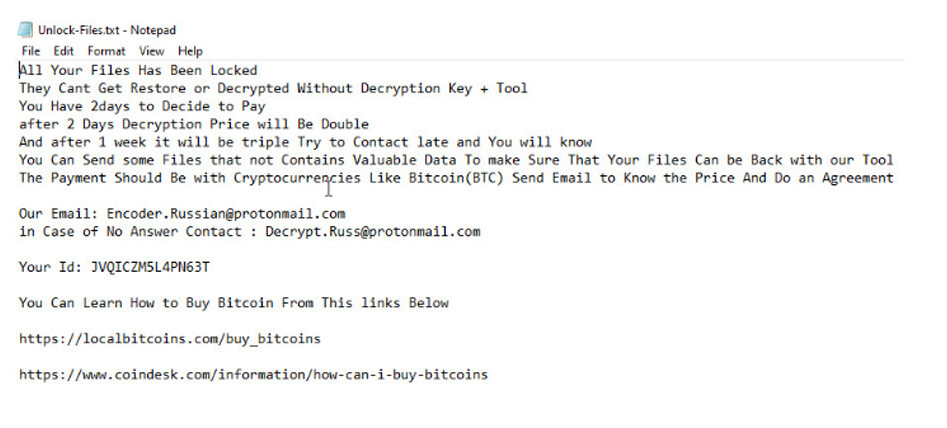
Unlock-Files.txt is created in every directory and has the instructions needed to decrypt the files.
Communication with C&C
Upon first run, the ransomware communicates with the C&C server 92.222.149.118. It contacts it in TCP port 170 and sends the following data:
- Infection ID
- Encryption key
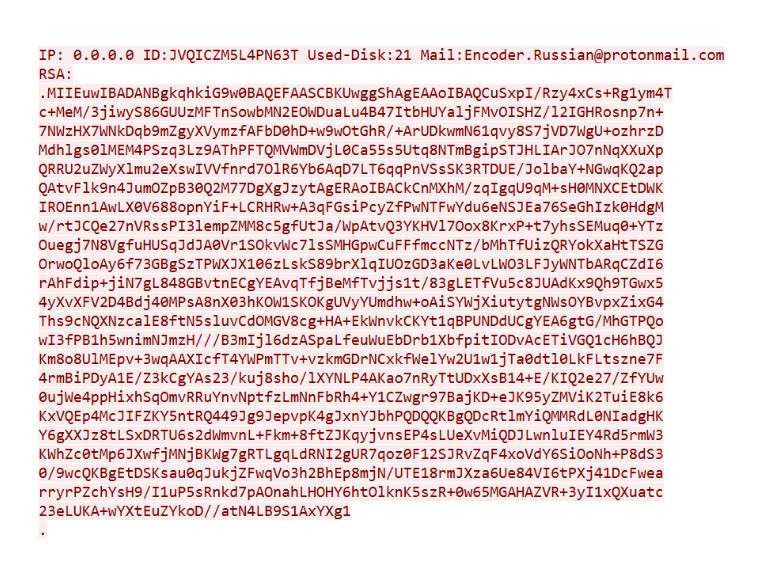
Once the encryption is finished, it contacts the C&C again via ftp and downloads an executable called uiapp.exe. The C&C has currently been sinkholed, therefore the file is not available. This executable locks the computer and displays the ransom note.

Preventing Windows Recovery
Shadow copies is a technology that is included in Microsoft Windows that can create backup copies or snapshots of files or volumes. Odveta deletes all those copies at the end of the encryption to make sure recovery is not possible. It does that using the following command
vssadmin delete shadows /all
Ransomware Propagation Techniques
The ransomware doesn’t automatically propagate and is normally used during targeted attacks and is dropped manually or by other hacking tools.
Indicators of Compromise (IOCs)
- All files are encrypted with the following format: [filename].Email=[Email]ID=[infection_id].odveta
- Communication with C&C Server: 92.222.149.118 (TCP ports 170 and 21)
- Emails sent/received with the e-mail address Encoder.Russian@protonmail.com
Analyzed Sample SHA-256
042f4e04042db2edac2a808fd948ccf9558d2f238257a7af51ea762016f59098


