SunBurst - The Cyber Attack on SolarWinds
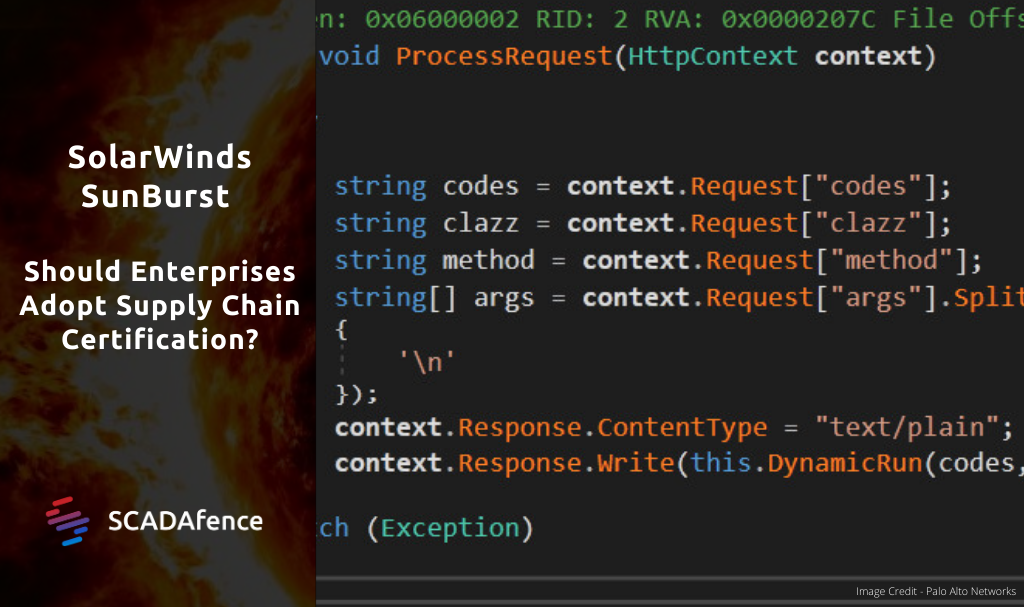
SunBurst is a cyber espionage campaign that leveraged a supply chain attack on SolarWinds, a leading supplier of network management software. Between March and May 2020, the attackers gained access to SolarWinds’ build system, added a malicious DLL (library) file, and distributed it to 18,000 SolarWinds Orion customers.
The malicious file allowed remote control of the target host, while leveraging advanced evasive tactics. Using this access point, the attackers were able to hack into organizations with well-established security practices such as Cisco and Microsoft. These organizations failed to detect the attack before FireEye (who was also attacked) made it public.
A targeted attack at this scale doesn’t happen very often. It’s a rare event that should shake both enterprises and the security community. The fact that this campaign went undetected for such a long period of time (6+ months), proves that something is fundamentally wrong with the way that computer networks are protected.
The success of this attack campaign, versus other campaigns, is built upon two factors:
- First and foremost, this is not a coincidence. This is a team of highly skilled attackers who made all of it possible. The campaign shows world-class planning, knowledge, experience and attention to detail.
- SolarWinds Orion is a network management product. Due to its role, it has a number of advantages as an attack source, vs. other types of attack sources:
- It’s whitelisted to perform reconnaissance (network monitoring) in many security tools - This tool is designed to perform reconnaissance, so no one will suspect when the tool does what it was designed to do.
- From SolarWindows Orion’s perspective in the network, the network is usually flat. Regardless of how many network segments are there, the component in Orion that scans the network requires direct network access to the target devices, so enterprises allow this traffic through their firewalls. This allows unique network access from the initial access point.
- SolarWinds Orion commonly has access to certain admin credentials that make it possible to move laterally.
The Supply Chain Risk
The supply chain risk to both enterprises and government organizations has been discussed in the last few years. The attack on SolarWinds is one of the most powerful examples of the supply chain risk. It joins a list of similar events such as the attack on Target in 2013. Supply chain attacks exploit trusted third-parties to enable access to a large number of attack targets in parallel. By using that trust, such as the trust organizations put on SolarWinds software updates, it’s easier to obtain access rather than attacking each target separately and directly.
Supply Chain Certification
The United States DoD (Department of Defense) is one of the government organizations that took far-reaching steps to reduce the supply chain risk. In October 2016, the DoD first issued a supplement to the DFARS regulation, that introduced cyber security requirements for DoD suppliers. In November 2020, only a month before the supply chain attack on SolarWinds, the DoD made another major addition to DFARS. This addition is called CMMC or the Cybersecurity Maturity Model Certification.
The CMMC includes a few non-linear improvements vs. the original DFARS supplement, in multiple categories:
- Third-party certification of suppliers by approved parties (C3PAOs) instead of self-certification.
- Certification is mandatory to be able to participate in RFIs and RFPs, meaning that it can affect the supplier’s revenue.
- CMMC has a 5-levels maturity model.
- There are 154 new requirements out of 171 in CMMC (vs. the original DFARS supplement), and they’re spread across the 5 levels of maturity.
- Reporting of compliance status in an online portal. This means that the DoD can monitor compliance of the entire DIB (Defense Industrial Base - the regulated organizations).
By introducing CMMC, the DoD conveys a clear message to DoD suppliers: We want you to be secure. And if you’re not secure enough, you cannot work on defense projects. Find another niche that’s less critical. If you want to work with the DoD, these are our requirements.
The question is: Should enterprises follow a similar path? Should a supply chain certification model be the standard in enterprise RFIs and RFPs?
The Pros and Cons of Supply Chain Certification
There are a few pros and cons to consider when discussing secure supply chain certification.
Pros:
- Increased security of the supply chain using financial incentives.
- Competition between suppliers on security maturity levels - Enterprises will start ranking suppliers based on a new metric.
- Transparency in security maturity levels. "Are you a Level 3 Security supplier or a Level 5 Security supplier?"
- Following a cyber attack, the certification might be re-evaluated. If major violations are found, the certification can be voided.
Cons:
- How much is this going to increase the prices of goods and services? And is it worth it?
- The certification can end up being another checkbox, where it has high costs and provides no security value.
- Smaller suppliers might find it difficult or impossible to be certified within their resources, which will create a bias toward larger organizations.
- Do enterprises have a large enough negotiation power, similar to that of the DoD, to pose such requirements on suppliers?
Our Predictions
We see a clear path to how supply chain certification becomes mainstream in the next years. With the DoD adopting CMMC, certain suppliers will have a CMMC certifications. They can then use their CMMC certification as a competitive advantage in non-DoD deals.
The DoD kickstarted this program, defined the requirements, and laid out the infrastructure (C3PAOs, RPs, etc). That allows the entire world to adopt CMMC - other government bodies and enterprises can easily adopt it at a low cost.
If the CMMC certification will be perceived as an efficient risk reduction strategy, and that there’s nothing fundamentally wrong about it, this (or a similar) model is going to expand into additional industries.
The SCADAfence Governance Portal is a compliance monitoring automation platform from SCADAfence, that automatically monitors your network’s compliance with the major cyber security standards and regulations. If you’re interested in learning more about how to measure and increase your security program maturity, please visit this page for a short demo about this product.