The Cyber Kill Chain is a framework that outlines the stages of common cyberattacks and the points in the process at which attacks can be detected or intercepted. Developed by Lockheed Martin, this model contains seven phases: reconnaissance, weaponization, delivery, exploitation, installation, command and control, and actions on objective.
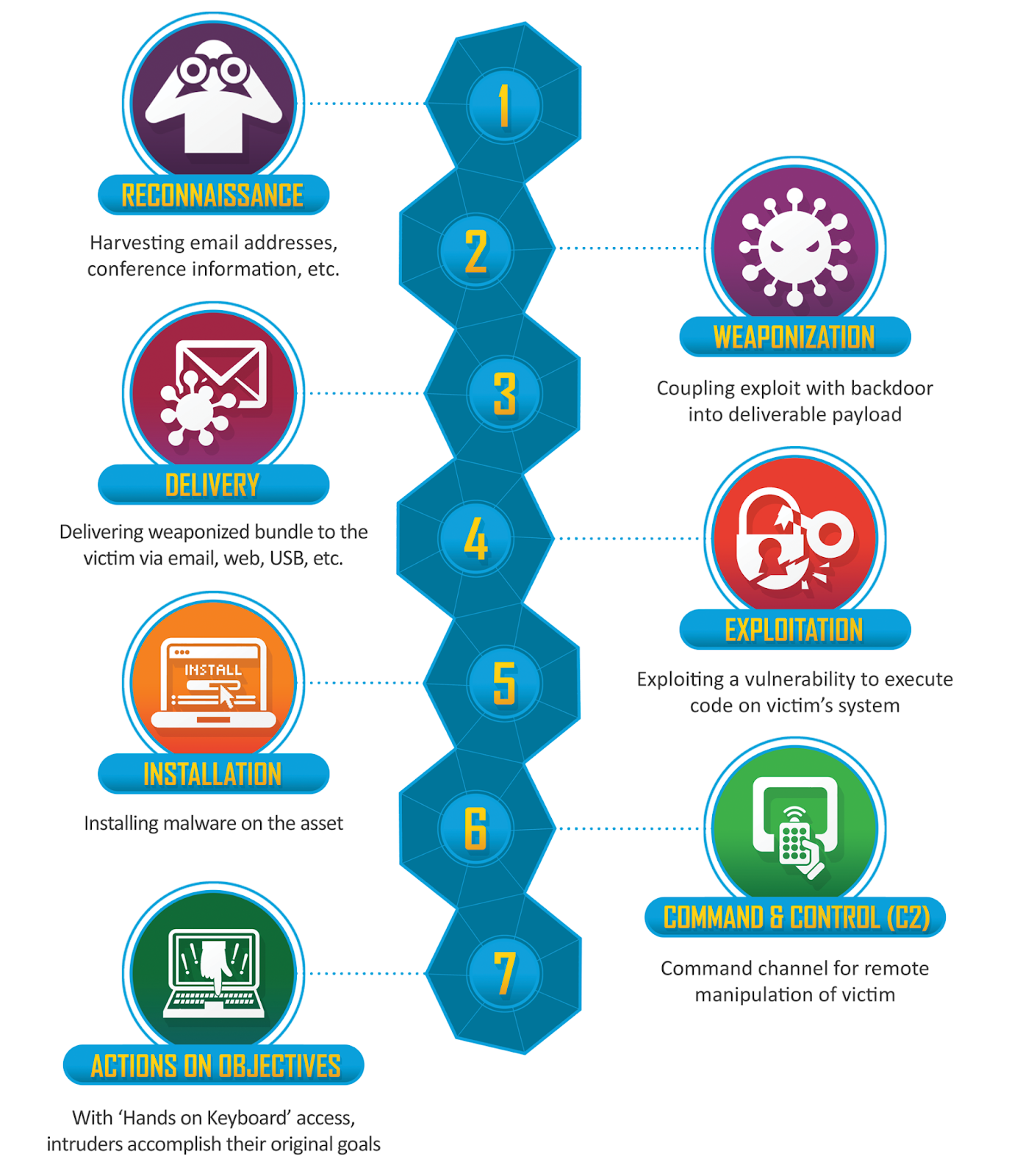
Image: Cyber Kill ChainⓇ- Lockheed Martin
Post-exploitation refers to any actions taken by an attacker following the exploitation phase. Attackers, both legitimate pentesters, and attackers with malicious intent, use the post-exploitation phase for privilege escalation, persistence in the network, lateral movement, command and control, data exfiltration, and more.
In the past, attackers would develop custom payloads to target different systems written in various languages. More recently, attackers started using Rapid7’s Metasploit, a free, open-source penetration testing framework. It quickly became the default post-exploitation tool used to find vulnerabilities on networks and exploit them. Attackers like Metasploit because it is free of charge, easy to use and highly customizable.
Now, we are starting to see profit-seeking malicious attackers willing to pay a premium for access to such frameworks, sometimes even thousands of dollars. They want to leverage the frameworks’ capabilities and demand for a higher payout following the execution of their attack. This has led to the transition to Cobalt Strike, a commercially available adversary simulation software. Cobalt Strike has become increasingly popular among attackers and is replacing Metasploit as the post-exploitation framework of choice.
Attackers often use penetration testing tools, such as Metasploit and Cobalt Strike, for malicious purposes. Such software gets wielded in standalone attacks, and sometimes also at scale against multiple endpoints simultaneously.
Uses of Post-Exploitation Attack Frameworks
One use for post-exploitation frameworks is pushing payloads directly to infected endpoints, so attackers can assess the endpoint and see if they wish to escalate the attack. In other instances, attackers use these tools for lateral movement, in which case the endpoint serves as the starting point for a wider attack. During these attacks, attackers will typically attempt to escalate privileges, access Active Directory Domain Controllers, and use that access to steal sensitive data or infect systems with crypto-locking malware.
These frameworks manage connections with targets using Command and Control Servers, also known as C2 or C&C, which are tools and techniques attackers use to maintain communication with compromised devices following initial exploitation. Depending on the attack, C2 generally involves one or more covert communication channels between the attacker's platform and devices in a victim organization. Using these communication channels, the adversary can issue instructions to compromised devices, download additional malicious payloads, and pipe stolen data back to the adversary.
Publicly available hacking tools, such as Metasploit and Cobalt Strike, are used as post-exploitation tools with various malware droppers responsible for the initial infection stage. The most common malware droppers are IcedID, ZLoader, QakBot, BazarLoader, and TrickBot.
Cobalt Strike Tool - The Falling King of Attack Frameworks?
As discussed above, Cobalt Strike is a popular penetration testing tool widely used by malicious threat actors to launch real attacks against organizations’ networks. This attack framework combines social engineering, unauthorized access tools, network pattern obfuscation and a sophisticated mechanism for deploying malicious executable code on compromised systems.
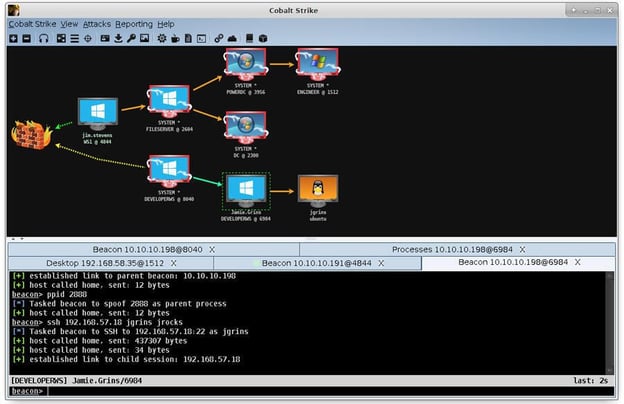
Cobalt Strike Screenshot
Cobalt Strike uses an agent named “Beacon” to gain a foothold in a target network, then download and execute malicious payloads. It can be transmitted over HTTP, HTTPS, DNS, or SMB. It can perform both low-profile asynchronous communication and real time interactive communication with the Cobalt Strike server.
Beacon has the ability to modify its network signature, using C2 profiles to appear as another attacker, emulate the behavior of various malware, or masquerade as legitimate traffic.
Cobalt Strike is routinely in the headlines, and that trend will likely continue, as the tool is both powerful and notoriously difficult to detect. However, over the past few years, original and cracked versions of Cobalt Strike have been so heavily abused by threat actors and ransomware gangs that it has become easier for security teams to detect. Its popularity and increased usage has made defending against it more efficient, and threat actors have been observed developing new, even more complex attack frameworks and deploying them as alternatives for Cobalt Strike.
Further, Cobalt Strike was used in multiple ICS related attacks including organizations in the government, healthcare, manufacturing, logistics, hospitality, and media sectors in the US as well as China, India, Taiwan, and Vietnam.
Types of Attack Frameworks and Post-Exploitation Tools
BRc4 - The Main Claimant to the Crown
Brute Ratel is the most advanced Red Team & Adversary Simulation Software in the current C2 Market. It not only emulates different stages of an attacker kill chain, but also provides a systematic timeline and graph for each of the attacks executed to help validate the attacks and improve the internal defensive mechanisms.
Brute Ratel uses Badgers for remote access, similar to Cobalt Strike’s Beacon. Badgers support egress traffic over HTTP, HTTPS, DNS Over HTTPS, SMB and TCP. It connects back to the Brute Ratel Server periodically, fetches tasks queued on the Ratel server, runs them and returns a response. Badgers communicate to each other and to the server over a custom encrypted channel for all types of badgers.
This tool is uniquely dangerous since it was specifically designed to avoid detection by endpoint detection and response and antivirus tools. Its effectiveness is demonstrated by the small number of detections reported by vendors on VirusTotal, an open access tool for analyzing and sharing information on suspicious files, domains, IPs and URLs and detecting malware and other breaches.
Because of Brute Ratel’s advanced capabilities, threat actors and ransomware gangs have been quietly transitioning to this tool for their attacks. Moreover, it has been reported that a cracked copy of Brute Ratel is now circulating among threat actors in online hacking forums, making this toolkit more accessible for wide usage.
This post-exploitation tool has been used by the Conti, Black Basta, and BlackCat ransomware gangs, and attacks using the tool are believed to have been conducted by the Russian state-sponsored hacking group tracked as APT29, also known as Cozy Bear.
Sliver
Sliver is an open-source, cross-platform adversary emulation/red team framework, written in GoLang. Cross-platform implants can be generated in several formats, including shellcode, executable file, shared library/DLL file or service. These implants can be obfuscated, rendering their detection harder. Sliver allows lateral movement using PsExec.
Sliver framework has been actively used by the FIN12 ransomware gang and state-sponsored threat actors such as APT29. Sliver has been deployed in more recent attacks using the Bumblebee malware loader, associated with Conti.
Manjusaka
Manjusaka is a Remote Access Trojan (RAT) family of malware composed of C2 written in GoLang and implants written in Rust. The implants consist of a variety of capabilities that can be used to control the infected endpoint, including executing arbitrary commands.
The RAT implants support command execution, file access, network reconnaissance, and more. The implants can execute arbitrary commands using “cmd.exe”, get file information, get current network connections, collect browser credentials, take screenshots, obtain system information, and activate the file management module.
The lure document, C2 menus, and the configuration options are written in Chinese, so it is safe to assume that its developers are based in China. It is likely that Manjusaka will be deployed in the campaigns of multiple Chinese APTs soon, as threat groups from the country are known for sharing a common toolset.
Alchimist
This framework consists of a C2 tool dubbed 'Alchimist', a previously unseen RAT called 'Insekt', tools such as a custom backdoor and malware for exploiting vulnerabilities in macOS, and tools such as netcat, psexec, and fscan. The framework is written in GoLang.
Manjusaka and Alchimist have virtually the same set of features. They both have been designed and implemented to operate as standalone GoLang-based executables that can be distributed with relative ease to operators.
Like Manjusaka, Alchimist developers are likely based in China due to the use of Simplified Chinese in the framework.
Impact Assessment
Next-gen frameworks provide ever-growing capabilities and can evade classic detection by establishing rogue communication channels to transmit further instructions.
These frameworks have been deployed as alternatives to the widely abused Cobalt Strike, or parallel to it for redundancy. The migration from Cobalt Strike to freely available tools is seen as an attempt to decrease adversaries chances of exposure in a compromised environment and render attribution difficult, giving their campaigns more stealth and persistence.
Although widespread usage of some of these frameworks hasn’t been observed in the wild at this point, they all have the potential to be adopted by threat actors all over the world.
SCADAfence's OT Security Best Practices
The best defense against post-exploitation attack frameworks is a comprehensive OT security protection solution that can detect the communications between the framework’s implants and the C2 server, as well as the changes executed by the implants.
The SCADAfence Platform has all these capabilities. Moreover, the Platform detects the use of Cobalt Strike, mimikatz, PsExec, and other tools used by these frameworks for various stages of an attack. At a U.S. government sponsored event earlier this year called Hack The Port, SCADAfence effectively demonstrated its ability to successfully defend against these attacks. Download the report for more details.
SCADAfence recommends taking the following measures to minimize the risk of exploitation:
- Limit Network Exposure – minimize network exposure for all of your control system devices and/or systems, and ensure they are not accessible from the Internet.
- Monitor Network Traffic – monitor access to the production segments. In your network monitoring tool, create logical groups of the affected devices and define traffic rules to alert on suspicious access to them.
- Monitor User Activity – if you’re a SCADAfence customer, you can use the SCADAfence Platform to monitor access to the affected devices and track all of your user activities using the User Activity View. RDP and SMB connections can be tracked in an attempt to discover malicious activity.
- Connect to the SCADAfence Cloud – if you’re a customer, connect your SCADAfence Platform to the SCADAfence Cloud to get the latest security updates.