In 2021, the increasing number of cyber security attacks on major critical infrastructure operators grabbed the headlines. The successful attacks targeted different industrial sectors such as oil pipelines, food manufacturers, and water and wastewater facilities. Up until these attacks occurred, the media and the industrial sectors paid little attention to the cybersecurity of critical infrastructure.
Now that organizations and analysts are increasing their awareness of the different risks and vulnerabilities with critical infrastructure and OT environments, it is becoming more visible and how impactful these risks have on our daily lives. The recent increase of attacks on the different industrial sectors is finally receiving attention including at the highest levels of several governments.
In May 2021, the President of the United States Joe Biden issued an Executive Order on improving the nation’s cybersecurity with a clear focus on critical infrastructure. As stated, “The scope of protection and security must include systems that process data (information technology (IT) and those that run the vital machinery that ensures our safety (operational technology (OT).”
While this is a great first step into advancing OT security, it is simply not enough. The different risks are due to three key factors.First, more critical infrastructure operators are digitalizing their equipment and environments which is resulting in their organizations becoming more vulnerable to cyber attacks. Second, the trend of converging IT and OT to be more interconnected has resulted in IT exploitation which is affecting secure OT environments. Last but not least, cyber criminals and nation-state attackers are attacking more aggressively by adopting more sophisticated tactics to exploit industrial control systems (ICS).
The Growing OT Attack Surface
As operational technology (OT) networks are becoming increasingly connected to an organization’s network infrastructure, older strategies such as ‘air gapping’ are no longer relevant or feasible.
Many organizations think IT security best practices are the answer and will search for IT security solutions that could possibly integrate with their OT environments. This is the wrong approach to gain visibility and threat detection into OT networks. OT networks need a specifically designed solution that can detect security risks to avoid the exploitation of critical infrastructure. By deploying the wrong kind of solution within an OT environment it can result in different problems occurring to the OT network such as downtime and false-positive alerts and more.
Instead, organizations should deploy OT security solutions that are designed and integrated with Zero
Trust capabilities. This is the idea of limiting access to users, devices and equipment with
out the proper identification and permissions. So how does the Zero Trust model relate to OT networks?
Zero Trust For OT Networks
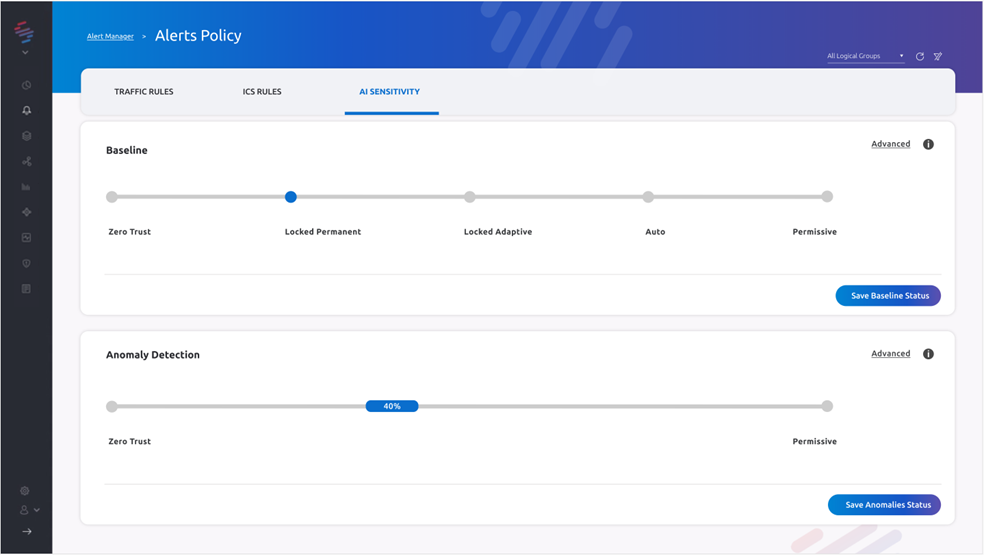
Diagram 01: The SCADAfence Einstein Baseline’s Sensitivity Dashboard
The Zero Trust motto is “never trust, always verify” and this is especially true when creating security controls in OT networks and devices.
Many OT devices and systems are still using un-encrypted and unauthenticated protocols. However, it’s not just the devices. Too often, OT teams are not open to the idea of connecting their once-isolated systems or PLCs to the Internet, despite those systems being implemented with encryption and authentication. As more IT and OT systems are opening their gates to connect to the Internet, the need to adopt the principle of less privilege is more aligned with the expanding threat landscape.
Organizations need to look at OT security solutions that can provide policy-based access for authorized users. This is the approach that only OT teams or other specific users should have access to OT environments. Simply put, only employees who need access to OT networks and devices to do their day-to-day job should have access.
Enforcing access controls early on, which is based on the principle that no one should be able to connect unless authorized, will allow security teams to provide access once authorized. Each user and device access request needs to be verified and then, only if verified, the access will be granted to the authorized users.
By implementing the Zero Trust security model with granular access authorization, it can guarantee organizations that the proper access is being granted in OT environments with an additional level of security. By restricting who has access to what network or device, the Zero Trust model will help minimize the attack surface of the increasing risks within an OT environment.
Additionally enforcing MFA (multi-factor authentication) is another essential Zero Trust model capability for OT leaders to implement with role-based access. With MFA, access is only granted after successfully presenting two or more pieces of evidence, or factors, to an authentication mechanism. These factors will provide an additional layer of security against unauthorized access for OT environments.
While the task to integrate the basic Zero Trust framework is not a simple task across complex environments like OT networks, rethinking a security approach with the Zero Trust framework is the right step in protecting critical infrastructure and OT environments.
SCADAfence Offers Zero Trust Capabilities for OT Environments
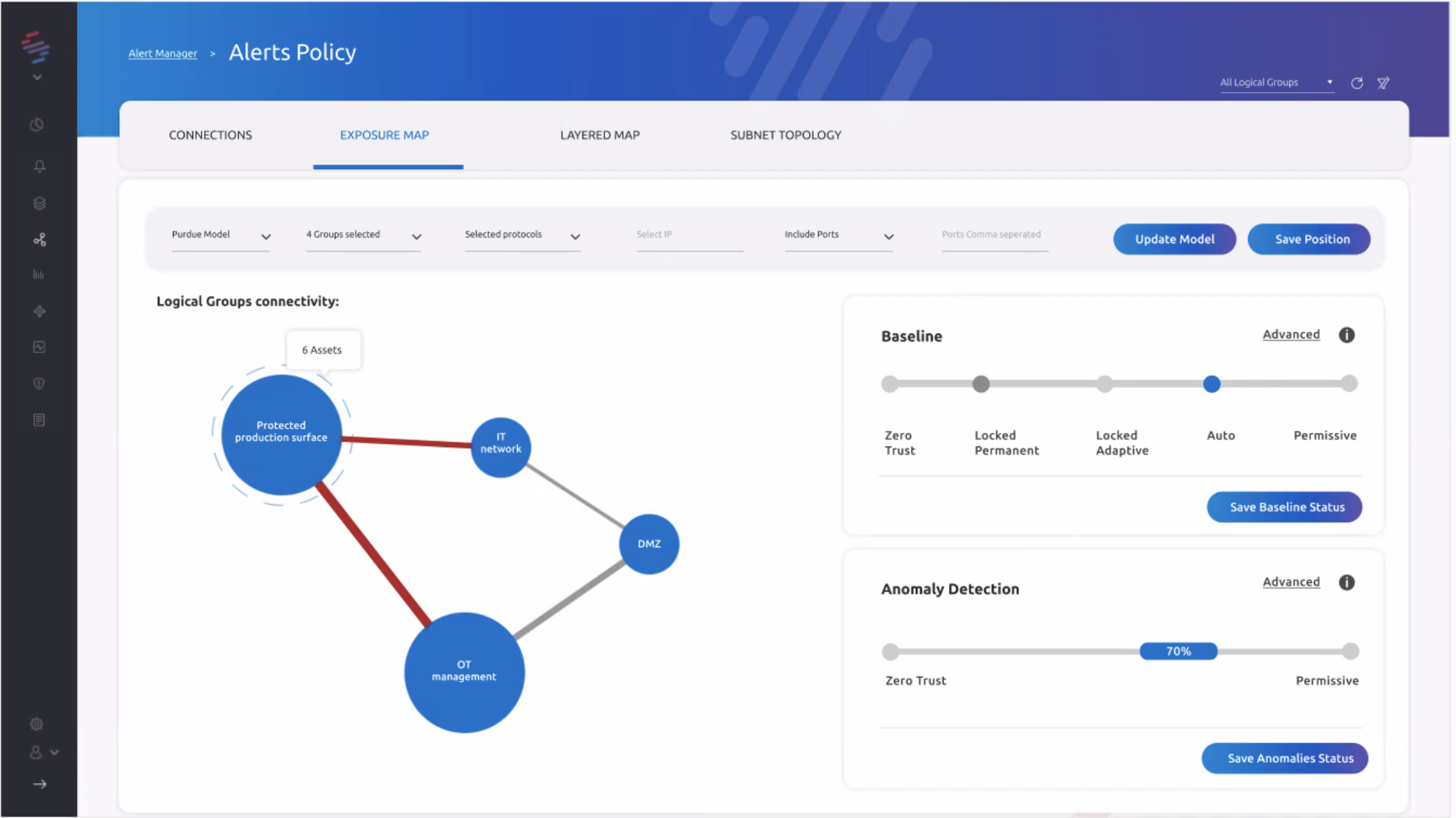
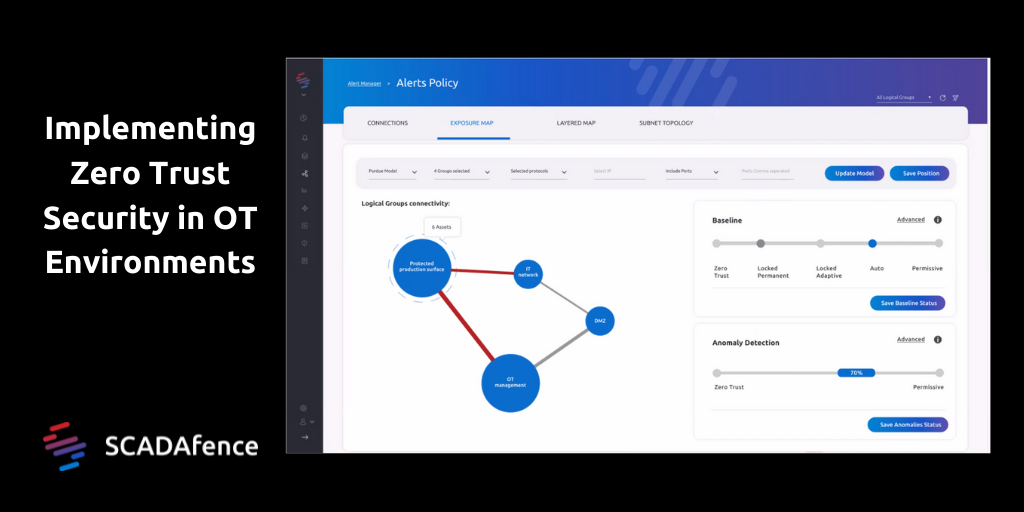
Diagram 02: The SCADAfence Einstein Baseline’s Unique Zero Trust Capabilities
SCADAfence is the only OT security vendor offering an OT network security solution that integrates with the Zero Trust model for industrial environments. The SCADAfence Platform enables users to define access-group segmentation and to enforce Zero Trust capabilities in their OT networks. Users can gain full visibility of their production networks which are designed and supported by the Zero Trust security framework.
With the industry-leading Einstein baseline, the SCADAfence Platform learns an entire industrial network in less than 2 days. This includes learning all traffic patterns, asset behavior and network subnets. The Platform is able to immediately send alerts on any anomalies or deviations from the normal network behavior.
When the Zero-Trust model is enabled in the Einstein baseline period, the Platform not only displays and alerts users of all the activities and devices on the network, but all network behaviors are treated as potentially malicious until further verified.
As we continue to advance our leading OT security platform with more security features and capabilities, SCADAfence users continuously have more flexibility to manage their OT environments. Our latest integration of Zero Trust capabilities, will guide users with an additional level of security from the baseline stage to the ongoing security management stage and onward.
To learn more about SCADAfence's Zero Trust capabilities for OT networks, schedule a demo with one of our experts here: https://l.scadafence.com/demo