On May 8th, news broke that Colonial Pipeline, one of the largest fuel pipelines in the US, was forced to stop all operations due to falling victim to a ransomware attack. The attack on Colonial Pipeline, which supplies close to half of the oil and gas used on the East Coast, is just the latest example of why cybercriminals target the oil and gas sectors.
Colonial Pipeline Struck by Ransomware
According to a report by The Wall Street Journal, Colonial Pipeline, the operator of the biggest gasoline pipeline in the United States was forced to shut down operations late May 7 following a ransomware attack. The cybercriminals threaten to roil energy markets and upend the supply of gas and diesel to the East Coast.
Colonial Pipeline is a key passage for the eastern half of the United States. It’s one of the main sources of gasoline, diesel and jet fuel for the East Coast with a capacity of close to 4 million barrels a day. They published a statement Saturday saying they were victims of a ransomware attack that affected their corporate IT network. This attack didn’t exploit their operational network that controls its pipelines and distributes fuel which is separate from the corporate network. Colonial Pipeline announced they did indeed shut down the pipelines as a precaution to prevent the attack from spreading.
Initial thoughts led many people in the security industry to believe that this was another attack by a foreign government. However, Bloomberg published a report on Saturday, May 8th that the attack appeared to be spearheaded by the ransomware group called DarkSide. Known for their "double-extortion" schemes, Darkside took nearly 100 gigabytes of data from Colonial’s network in just two hours on Thursday.
The attackers threatened Colonial Pipeline that if the ransom was not paid, they would leak all the stolen data to the internet, encrypt the data on the attackers’ computers and Colonial’s network would remain locked. It’s not clear how much money the cybercriminals are asking for and how the attackers exploited their network. One thing that is clear, is that this attack is a concrete example that cybercriminals are moving their attention to attacking industrial organizations regardless of size or sector.
Oil & Gas Industry is an Attractive Target
Over the years, the oil and gas industry has steamrolled into becoming one of the most powerful and economical global industries as it is critical for global and national economies. This has created a major target on their back, as adversaries see these sectors as valuable targets to exploit Industrial Control Systems (ICS) vulnerabilities. In the past, operational technology (OT) needed in oil and gas operations was isolated and "air-gapped," and today these operational technology networks are connecting more often to different IT infrastructures and to the internet which has created a new door for attacks. The convergence of OT and IT environments in the oil and gas operations has created an endless amount of vulnerabilities from both the IT and the OT environments. There are also emerging risks from Internet-of-Things (IoT) devices and ongoing and growing priorities centered on compliance.
As seen in recent attacks on gas and oil organizations such as Pemex and Colonial Pipeline, it is justifying how attackers have gained an interest in the industry from understanding the different behaviors to how to exploit the organizations. This has resulted in oil and gas organizations needing to protect against any method of cyberattacks to ensure the global economy and civilian safety is not affected due to an attack.
Protecting Oil and Gas Operations
While in the case of the Colonial Pipeline attack, the details of how the adversaries successfully exploited their corporate network are not public yet, it has brightened the light that now is the time for gas and oil organizations to implement a strong OT security strategy.
Last month, the NSA released a report describing the importance of protecting industrial control systems (ICS) and operational technology (OT) from cyber attacks. In the report the NSA states, “Without direct action to harden OT networks and control systems against vulnerabilities introduced through IT and business network intrusions, OT system owners and operators will remain at indefensible levels of risk.”
Additionally, the NSA report expressed that organizations and operators need to protect critical operations. “While OT systems rarely require outside connectivity to properly function, they are frequently connected for convenience without proper consideration of the true risk and potential adverse business and mission consequences. Taking action now can help improve cybersecurity and ensure mission readiness.”
Before the NSA advisory released this report of their recommendations, many oil and gas organizations have taken the right measures to secure their OT systems and networks. Over the last seven years, SCADAfence has been working with many critical infrastructure organizations, including oil & gas operators to ensure their OT networks are safe and a proper cyber security infrastructure is implemented.. We provide them with full network visibility, accurate detection of any anomalous behavior and malicious activities - including anomalies that originate from ransomware attacks.
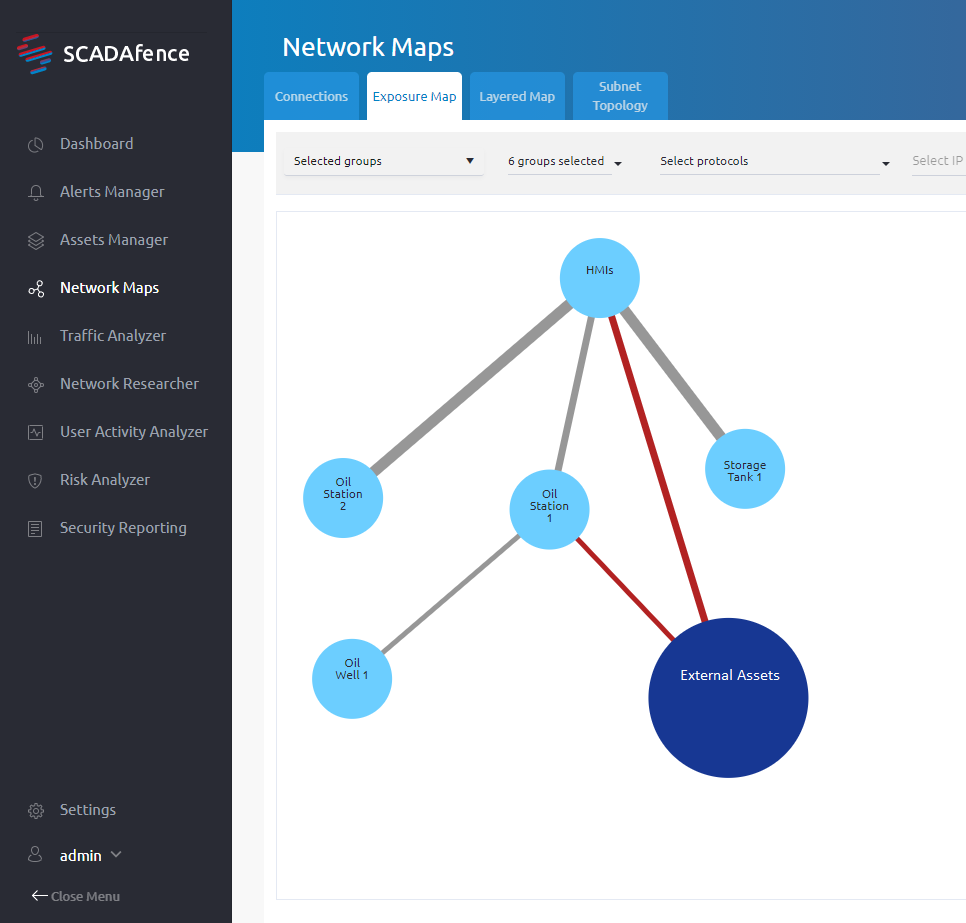
The above diagram shows how OT Security vendor SCADAfence helps organizations in the Oil & Gas and pipeline industries to have full visibility between their IT and OT networks. This lets them know where the attack vectors are located and they can identify all of the connections between these networks with pinpoint accuracy. This approach has helped hundreds of organizations to successfully mitigate any anomalous activities on their operational networks, which can later turn into a cyber attack.
In an Operational Technology World, Failing to Plan = Planning to Fail
Basic cybersecurity practices can help to prevent these attacks going forward. This includes getting visibility into the entire network, as it’s hard to protect what you cannot see. Additional security practices include network segmentation or even micro-segmentation if possible, and getting continuous network monitoring is even more crucial in preventing similar attacks going forward.
Numerous oil & gas operators have already adopted continuous network monitoring and threat detection technologies to gain increased visibility into their OT networks and keep their critical infrastructure networks secure.
With this holistic approach, of network monitoring, anomaly detection, remote access visibility, and compliance, many oil & gas organizations are already reducing 95% of their risk level of future attacks.
A key element of these solutions is that they are all agentless, not intrusive, and can perform superhuman tasks at a fraction of the cost of one human worker.
If your organization is looking into securing their industrial networks, download our case study with a fortune 100 Oil & Gas Industry Leader to learn how SCADAfence provides complete visibility in their OT networks and provides real-time threat detection of any malicious activities.


.png)